What is TOR and is it safe to use TOR?
You may have heard of it: TOR. It is an abbreviation for The Onion Router. What kind of weird name is this? We hear you saying it already. Yet it is a very creative name with a logical meaning.
TOR is praised to the skies by those who crave online privacy and freedom. But what exactly is TOR? How does it work? And is it safe to use TOR?
The genesis of The Onion Router
The Onion Router was not developed lightly. Computer scientist Rodger Dingledine began developing TOR on behalf of the U.S. Navy and the U.S. research division darpa.mil (Defense Advanced Research Projects Agency). The purpose of Tor: secure internal communications between military personnel.When
Dingledine developed The Onion Router back then, he did not intend to set up a Valhalla for cybercriminals and hackers, which The Onion Router is known for today, among other things. Therefore, the question “Is it safe to use TOR?” is certainly not an unnecessary one.
What exactly is TOR?
Over time, TOR has grown into a nonprofit organization. TOR’s focus is on researching and developing privacy tools.
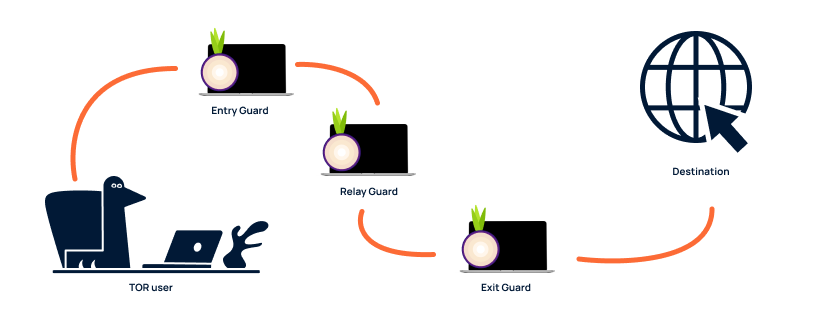
Those who use TOR experience the benefits of anonymous Internet browsing. Your Internet traffic is rerouted through TOR servers, also known as TOR Nodes so that your identity can no longer be traced. During the journey that your Internet traffic makes to the final destination, the Internet traffic passes several TOR-Nodes.
Guard Node
The first stop your Internet traffic makes is at the Guard Node. The Guard Node only knows who the Internet traffic is coming from. The Guard Node does not know the content of the Internet traffic.
Exit Node
The end station of your Internet traffic is the Exit Node. Through the Exit Node, your Internet traffic eventually reaches the Internet. The Exit Node works the opposite way to the Guard Node. The Exit Node can decrypt your Internet traffic but does not know from whom the Internet traffic originates. Therefore, your identity cannot be traced in the end.
Relay Node.
During the route your Internet traffic travels between the Guard Node and the Exit Node, your Internet traffic passes one or more Relay Nodes. The Relay Nodes do not know the content of the Internet traffic. All the Relay Nodes know is who the Internet traffic is coming from, and where the traffic is going.
Anonymity on the Internet sounds like music to your ears. But is it safe to use TOR? We can’t say a resounding “YES” to that. There are too many snags in the TOR network that compromise your security.
The Layer of Truth
Why exactly is it called The Onion Router? When you send your Internet traffic through TOR, the Internet traffic passes through multiple TOR Nodes. Each TOR-Node offers a new layer of protection, just like an onion has many layers. When your Internet traffic reaches the Exit Node, it is time for the layer of truth. The final protection layer shows only the decrypted Internet traffic. No more, no less.
What can you use TOR for?
Most people use TOR to surf the Internet anonymously and safely. Another reason people use TOR is to access websites that are blocked.
TOR does not only allow access to blocked websites. You can also visit web addresses within TOR’s network. These web addresses do not end in .nl or .com but in .onion.
.onion websites are called the deep web. This is because these websites cannot be found through normal search engines such as Google.
TOR is also a solution for those in countries where there is a lot of censorship. Think of countries like China and Russia.
TOR can be used in many ways, but it can also be abused in many ways. Therefore, extra protection is a must.
Is it safe to use TOR?
Tor offers endless possibilities on the Web. It is the ultimate browser for experiencing freedom on the Internet but there is also a dark edge to the browser. Is it safe to use TOR? To that, our answer is “NO.
We’ve said it before. The Onion Router has become a Walhalla for cybercriminals and hackers. And you, too, are a potential victim.
The key to the dark web
The dark web is a part of the worldwide web. It is just not possible to access the dark web through a normal search engine. TOR’s search engine provides the key to the dark web.
The dark web sounds like a dark black room in which you are inundated with images that are forever burned into your retinas. This is not so bad in reality. The dark web can mainly be compared to an illegal marketplace. From all kinds of firearms to large collections of drugs. You can find it on the dark web.
Playground for cyber criminals and hackers
Cybercriminals and hackers also like to hang out on the dark web. The dark web is a playground for cyber criminals and hackers where they leave viruses and malware (malicious software) here and there. All it takes is one click on the wrong link and the malware digs its way into your systems. Cybercriminals and hackers are like a kid in a candy store. The malware gives them access to all kinds of information that is worth gold to them. You are a cybercriminal’s or hacker’s revenue model, so they are happy to take advantage of your vulnerabilities.
Safe Internet browsing with a VPN
Surfing the Internet via the TOR browser offers anonymity on the Internet. But not only TOR offers true anonymity and allows access to websites that are blocked.
Anonymous surfing with a VPN connection
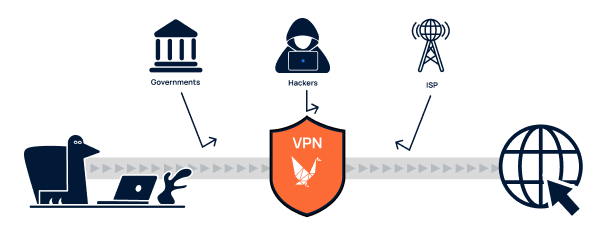
Those who want to surf the Internet anonymously can also use a VPN connection. A VPN connection is a secure connection between you and the Internet. By using a VPN connection, it is no longer possible for outsiders, such as cyber criminals and hackers, to sketch a profile of you and watch your Internet traffic. A VPN connection is therefore ideal for keeping prying eyes out.
Are you using a VPN connection? Then it’s safe to use TOR!
Get access to blocked websites.
In addition, you can use a VPN connection to access blocked websites. When you use a VPN connection, your Internet traffic is redirected through a VPN server. During this process, your IP address is shielded and your device is linked to the IP address of the VPN server. The VPN server can be located anywhere in the world. From America to the United Kingdom, the options are endless.
The adaptability of a chameleon
Are you connected to a VPN server in America? Then your device is associated with an American IP address. This makes it seem as if you are in America, and you can connect to the American version of Netflix, for example. A VPN also helps in countries where censorship plays a big role. Connect to a VPN server, in your home country for example, and still use all the websites you need.
Do you use a VPN connection? Then you have the adaptability of a chameleon. Just as a chameleon changes color in no time, you change location in no time with a VPN connection.
So a VPN connection not only provides additional protection when using TOR. You can even use a VPN connection as a replacement for TOR. Especially if you use TOR primarily to surf the Internet anonymously, and to visit websites that are normally inaccessible because of your location.
With GOOSE VPN, it is safe to use TOR
Using GOOSE VPN connections makes it safe to use TOR. GOOSE VPN is a 100% Dutch provider of VPN connections. We believe it is important that everyone can surf the Internet safely. GOOSE VPN’s VPN connections are therefore not only reliable and incredibly easy to use, but they are also affordable!
Cyber attack detection software
GOOSE VPN has more to offer than just VPN connections. You may have accidentally installed malware on your device while using TOR. Super annoying, so you want to get to it as soon as possible. That’s where GOOSE VPN’s Cyber Alarm helps! An extra feature you can purchase when you sign up for GOOSE VPN.
GOOSE VPN’s Cyber Alarm is cyber attack detection software. The alarm monitors your Internet traffic 24/7 for malware. As soon as the alarm detects a malware, you are notified immediately. This way you can counter the malware at an early stage. Unfortunately, it is not always possible to prevent cybercriminals and hackers from striking, but we can make it as difficult as possible for them!
Subscribe to GOOSE VPN now
Do you want to use TOR securely? You can! Sign up with GOOSE VPN now and receive a 30-day money-back guarantee!